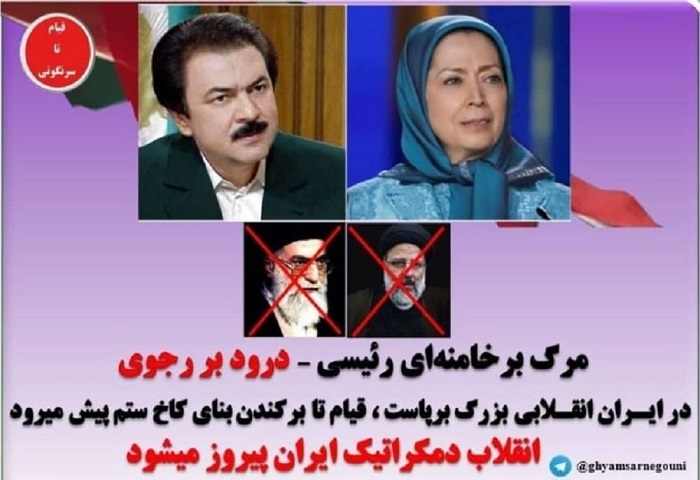

The group bypassed the regime’s digital safeguards, replacing images of Supreme Leader Ali Khamenei and President Ebrahim Raisi with those of Massoud Rajavi and Maryam Rajavi, leaders of the Iranian opposition. A stark message, “Death to Khamenei/Raisi! Hail to Rajavi!” was displayed on the defaced sites, a testament to the rejection and dissent present within Iran.
These cyber-attacks come on the heels of a similar disruption orchestrated by the same group earlier this month, targeting websites linked to the Iranian Foreign Ministry. The activists released over 50 terabytes of data previously protected within the regime’s servers.
The Associated Press noted on Monday that these attacks coincide with a series of embarrassing hacks targeting Iran’s state infrastructure, amidst rising tensions over its advancing nuclear program. State-run television, subsidized fuel pumps, and surveillance camera footage from a notorious prison have all fallen prey to these cyberattacks.
Secret Deals and Hostage Games: Leaked Documents Unveil Iran’s Attempts to Free Assadihttps://t.co/nJkH2M5RLN
— NCRI-FAC (@iran_policy) May 13, 2023
Despite silence from the Iranian state media and officials, the country is grappling with a series of devastating breaches affecting their nuclear program, state television, and surveillance systems. GhyamSarnegouni has been particularly forthcoming, revealing in-depth details regarding the disruption and defacement of Iranian presidency-affiliated websites.
Key revelations include gaining control over 120 servers within the presidency’s internal network, seizing command over the government’s server management network and server controllers, and infiltrating the presidency’s network of technical administrators. The hacktivists have also breached the “Users Internal Network,” gaining access to over 1,300 computers within the presidency’s network, classified internal communications, and tens of thousands of top-secret documents.
Specifically, GhyamSarnegouni has obtained entry into the encryption system responsible for classified messages, sensitive data regarding the presidency’s computer network infrastructure, classified documents outlining President Raisi’s foreign trips for 2023, and the identities of the 25-member security team safeguarding Iranian regime First Vice President Mohammad Mokhber.
The latest exploit, a widespread hack into Iran’s state-run TV and media, further illuminates the depth of the group’s penetrative abilities, unraveling the confidential exchanges and operations of the Iranian government. The substantial release of information by GhyamSarnegouni underscores the growing tide of resistance within Iran, signaling a potential shift in the country’s political landscape.
 MEK Iran (follow us on Twitter and Facebook), Maryam Rajavi’s on her site, Twitter & Facebook, NCRI (Twitter & Facebook), and People’s Mojahedin Organization of Iran – MEK IRAN – YouTu
MEK Iran (follow us on Twitter and Facebook), Maryam Rajavi’s on her site, Twitter & Facebook, NCRI (Twitter & Facebook), and People’s Mojahedin Organization of Iran – MEK IRAN – YouTu







