

By Armin Baldwin
The nationwide protests in Iran against the ruling theocracy erupted on November 15, 2019 and spread to 190 towns and cities with breakneck speed.
Many policy experts now view the uprising as a “turning point” since the regime’s establishment in 1979.
The use of technology, mobile devices and social messaging platforms played a significant role in helping the protesters to organize, exchange information between different locales, and get their message out to the rest of the world.
A new wave of domestic cyberwarfare, led by the Islamic Revolutionary Guard Corps (IRGC) in collaboration with the Ministry of Intelligence and Security (MOIS), accelerated significantly after the eruption of the nationwide protests.
MEK’s Internal Network
The internal network of the main opposition People’s Mojahedin Organization of Iran (MEK/PMOI), has established that the regime has focused on mass surveillance through malicious codes embedded in IRGC mobile apps to actively monitor and disrupt the communication of protesters and dissidents.
With the recent uprising, the Iranian regime is now complementing its network surveillance with stateful endpoint (mobile device) monitoring of content, context and contacts to counter the expansion of the uprising and to avert more protests.
MEK sources: IRGC establishes domestic mobile apps marketplace to spread spyware enabled apps: The homegrown market place, Café Bazaar, modeled after Google Play, is supervised by the IRGC. It is the IRGC’s platform of choice to promote and distribute spyware enabled mobile apps.
MEK sources: IRGC front companies are developing spywareenabled apps for cyber-surveillance and repression: Through front companies, such as Hanista, the IRGC has created apps such as Mobogram, an unofficial Telegram fork. Ironically, some of these spyware-enabled apps are available on Google Play, Apple Store, and GitHub, potentially exposing millions of users worldwide to the IRGC’s spyware and surveillance activities.
Iran’s universities
Iran’s universities have become a recruiting ground for IRGC cyberwarfare personnel. All recruits are hired through front companies that often engage in “research” activities with a few of the IRGC’s “handpicked professors.” These companies identify the needed talent for cyberwarfare.
Data shows nearly 48 million Iranians have smartphones and about 70% have access to the Internet. As the call for freedom and regime change grows louder in Iran, it is crucial to understand how the international community could stand on the side of the democracy movement by implementing effective measures to curb and confront the regime’s cyberspace repression of the Iranian people.
On November 21, 2010, Brigadier General Hossein Hamedani, the commander of the Mohammad Rasulollah base in Greater Tehran, announced: “The Bassij cyber council has trained over 1,500 cyber warriors who are now active.” He added that such activities would be stepped up soon. IRGC claims to have reached “the second [strongest] cyber army in the world.”
The Iranian regime is among a very few governments in the world where its testbed of cyberattacks and strategies is its own citizens. Experiments, test and optimization of IRGC’s cyberattacks on Iranians before deploying elsewhere is in line with Tehran’s longstanding worldview of instilling fear and repression at home while promoting terrorism, Islamic fundamentalism and chaos abroad.
According to MEK’s sources inside Iran, thus far, recruits have been hired through front companies, which often engage in “research” activities with a few of the IRGC’s “handpicked professors” and identify the needed talent for cyberwarfare.
In 2004, OpenNet Initiative conducted a research on Internet filtering in Iran and concluded “Iran has adopted one of the world’s most substantial Internet censorship regimes.” The report also pointed to “use of the filtering product” such as “Smart filter, developed by a United Statesbased for-profit corporation” and raised “questions about the complicity of western commercial firms in the filtering regimes of non-democratic countries.
During Iran nationwide November 2019 protests the regime had shutdown internet in order to block pictures and videos send by protesters.
Information and Communications Minister’s Key Role
Mohammad-Javad Azari Jahromi, the Minister of Information and Communications Technology, worked in close collaboration with the IRGC’s Intelligence organization, and its most senior official, Hossein Taeb, to take a series of extensive measures to regain control over all communications amongst the public and with the outside world. The IRGC took full control of the operations to execute these measures. The newly defined playbook included the following measures:
– Delay the access to Internet through speed limitation and connection throttling to cause severe slow speed and drive users away, given the cost of usage per minute.
– Cut off access to the global Internet in the affected areas where the uprising continued and spread, and then open the regime’s own “Halal Internet” for full control. This measure was first tested for several hours in Tehran.
– Interrupt mobile and SMS networks in the affected areas.
– Promote the use of spyware-enabled mobile apps such as Mobogram and other apps such as Telegram Farsi, Telegram Black, Telegram Talayi, Hotgram, and Soroush.
– Station plain-clothed IRGC agents from the cyberspace coordination office of the Intelligence Organization in communication centers in Tehran for surveillance and eaves dropping on mobile communications and social networks.
– Launch an extensive cyber PSYOP and social engineering efforts to lure users away from Telegram, promote rumors about those participating in the protests, spread fake news about no protests or cancelled protests, threaten users to leave channels related to nationwide uprising, spread fake photos amongst the various uprising channels and then discredit those channel for spreading fake news.
The regime’s cyberwarfare is primarily led by the IRGC. The Ministry of Intelligence (MOIS), and the State Security Forces (NAJA) also have cyberwarfare sections.
The IRGC’s central headquarters for cyberwarfare is known as the Ammar Cyberspace Base. IRGC’s cyberwarfare organization is under the command of the IRGC’s Intelligence Organization, which is headed by the cleric Hossein Taeb and his deputy, Brigadier-general Hossein Nejat.
The following organizational charts were compiled by the MEK’s network inside Iran, which demonstrates the new organizational alignment for the current wave of cyber repressions led by the IRGC.
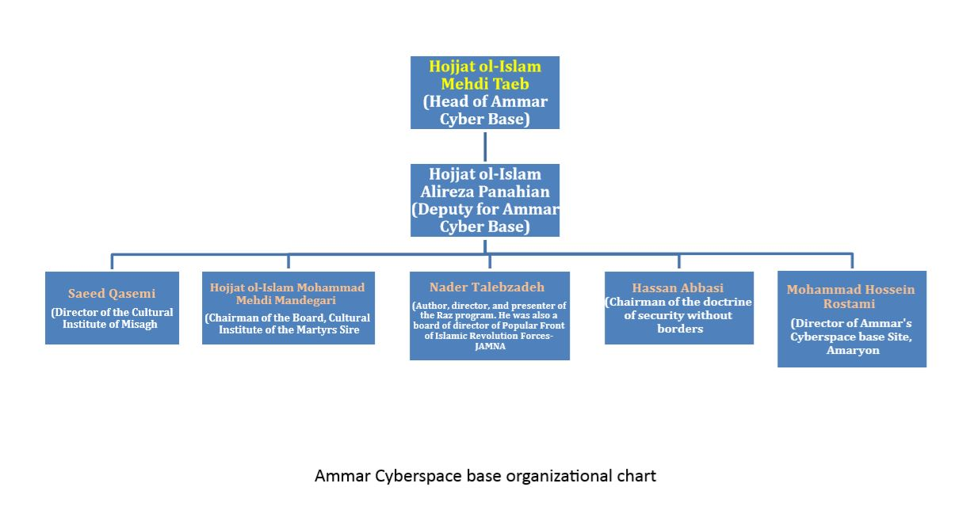
Ammar Cyberspace base organizational chart
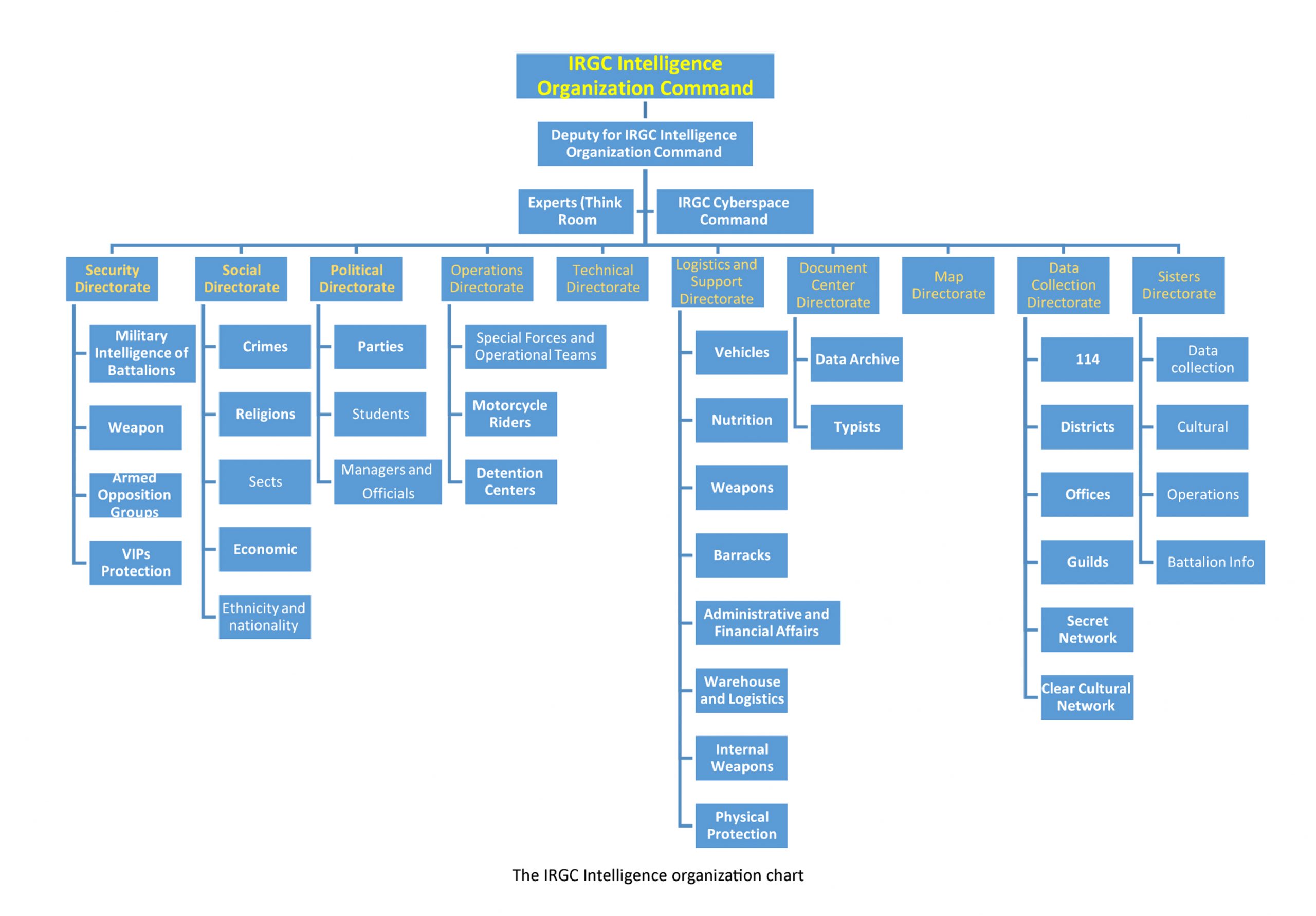
The IRGC Intelligence Organization Chart
The solution
What gives confidence to the Iranian regime to continue cyber repression is the international community’s inaction and ambivalence. As such, the European Union and the United States have added responsibility to act.
• Cyber repression by the Iranian regime must not be analyzed in a vacuum and separate from other repressive measure at home, export of terrorism and nuclear expansion. For this reason, in order to counter Tehran’s increasing cyber threats, a comprehensive and decisive policy must be adopted. Such a policy should include the full implementation of the current sanctions against the Islamic Revolutionary Guard Corps (IRGC) and its front companies, as well as imposing sanctions that would deprive the regime access to the international banking and financial systems. All measures necessary to evict the IRGC from the regional countries, especially Syria, must also be undertaken.
• All persons and institutions involved in cyberwarfare must be subjected to tough sanctions and denied access to the international market. While the clerical regime is denying the Iranian people access to Internet and the free flow of information, its massive propaganda machine, especially the state radio and television continue to spread false and misleading information. Iran’s propaganda machine is part and parcel of its machinery of suppression. It
must be subjected to comprehensive sanctions.
• The Iranian people need safe, secure, and free access to Internet. Additional circumvention tools are needed and should be offered as free services to the Iranians. These solutions should be scaled up to handle the traffic of millions of Iranian evading the regime’s surveillance, so that the Iranian people and protesters can continue to have unimpeded access to the global Internet service for the ongoing cyber resistance in Iran.
• Making apps and tools available in Farsi language will be a tremendous assistance that tech companies can provide to the people of Iran.
• Enforce security hygiene and measures in app market places. Prevent the proliferation of spyware-enabled apps by the Iranian regime, particularly those related to the IRGC. Remove all such known apps from the Internet.
• Enforce the Executive Order 13606 which clearly prohibits any entity to facilitate the Iranian regime in its “computer and network disruption, monitoring, and tracking” and “or otherwise provided, directly or indirectly, goods, services, or technology” that can be used to “enable serious human rights abuses by or on behalf of the Government of Iran,” and urge other western countries to do the same in preventing the Iranian regime’s cyber repression.







